Security and Privacy Issues in the 21st century
The Internet and 11 September 2001
Tom Worthington FACS
Visiting Fellow, Department of Computer Science, Australian National University, Canberra and Director of Publications For the Australian Computer Society
For the Bruce Hall Academic Dinner, 11 September 2002
This document is Version 1.2, 10 September 2002: http://www.tomw.net.au/2002/s112002.html
Abstract
Encryption technology, legal issues due to the international nature of the Internet, Transmission security, quantum computing, privacy of data have all become issues of public debate since the events of 11 September 2001. Tom Worthington has been a policy maker and public commentator on these issues as a technocrat at the Defence Department, as President of the Australian Computer Society, and more recently as an independent IT consultant and ANU Visiting Fellow. On 12 September 2001 he was contacted by the ANU Public Affairs Division and spent the next few weeks answering calls from the media on what the 11 September attack did to the Internet and telecommunications. This will be a first person account of someone who was on the other side of the world from New York, but was watching emergency operations live via the Internet through the traffic cameras in Manhattan. Tom Worthington argues that 11 September didn't change much, apart from bringing issues which IT professionals deal with on a dial basis to public attention.
One Year Later
A few days ago I was telephoned by Simon Hayes from The Australian newspaper recalling that we talked a year ago about the effect of the 11 September terrorist attacks on the Internet, telecommunications and information technology. There was speculation that there would be massive cyber attacks on the USA and its allies, including Australia. He asked why that did seem to have happened. The short answer is that attacks on the Internet are a daily routine occurrence. Security and related issues are something which IT professionals deal with on a daily basis.
Panning for Gold in the Research Stream
Before answering that I should explain who I am and what I do and don't do. It is a rare honor to be invited to speak at an academic dinner. I am not really an academic, but an information practitioner who works as an independent consultant. I have a background in government information technology implementation and policy. When I tell people that I am a Visiting Fellow at the Australian National University, I am asked "where are you visiting from?". The answer is that I am from the outside world; from the IT industry and I look at how research might be directed to useful ends.
Looking for useful technology in the research community is like panning for gold. You have to wade through some very chilly conditions and sift through mountains of dross to find a few specks of something valuable. Often what is of practical value is a mostly a byproduct of the research process and may not be considered of interest by the researchers. It may take decades of work and much more effort to turn a bright idea into a useful product. But often research can suggest new ways to use technology already available, which can be quickly and easily applied. However, computer scientists rarely take into account the human motivations which decide if a technology will be successful and actually used in practice.
Security technology is only of value if those who need to use it are motivated to use it properly. Indications are that not much has been changed by September 11. Advanced encryption systems are worthless if they are too difficult to use. Transmission security to protect your e-mail in transit is wasted if the recipient leaves paper copies lying around their office or electronic copies on an unprotected disk. Quantum computing may provide ways to beak existing security codes, but it is much easier to telephone the user, say you are from the computer support center and ask them their password. Also it is still common to see passwords written on notes stuck to computer monitors, although security conscious people write them under the keyboard. ;-)
Along with a global technology like the Internet must go a global mind-set. Having a global web site is of little value if you include your telephone number in an announcement, but neglect to include the area code. There is little point in relying on some local law to protect you on-line, when it may not be respected, or enforceable on line (whereas a on-line custom might do).
The Internet
 The Internet is a rare example of technology
which proved spectacularly successful and where
human motivations were taken into account. The story goes
that the Internet was developed with US defence funding to be able to survive
a nuclear war. The Internet was initially funded by
the military and has turned out to be useful for military purposes, but this was probably more by
accident than design.
The Internet is a rare example of technology
which proved spectacularly successful and where
human motivations were taken into account. The story goes
that the Internet was developed with US defence funding to be able to survive
a nuclear war. The Internet was initially funded by
the military and has turned out to be useful for military purposes, but this was probably more by
accident than design.
 The use of the Internet by the
Australian military was less than accidental. Like
the rest of the Australian government, the US and
UK, there was specific policy against the use of the Internet by the
Australian Department of Defence. It was considered
inefficient, insecure and unreliable. That
view changed rapidly in the late 1990's.
The use of the Internet by the
Australian military was less than accidental. Like
the rest of the Australian government, the US and
UK, there was specific policy against the use of the Internet by the
Australian Department of Defence. It was considered
inefficient, insecure and unreliable. That
view changed rapidly in the late 1990's.
 In 1995 when I prepared a web site for the Australian Defence Force Exercise Kangaroo
95, the Internet was still seen as a dangerous academic thing by much of the defence
community. But by 1997 when I prepared a web site for a joint Australian/US
7Th Fleet exercise, Internet technology was
starting to be in routine
use (although some of my military collogues
still refused to believe it).
In 1995 when I prepared a web site for the Australian Defence Force Exercise Kangaroo
95, the Internet was still seen as a dangerous academic thing by much of the defence
community. But by 1997 when I prepared a web site for a joint Australian/US
7Th Fleet exercise, Internet technology was
starting to be in routine
use (although some of my military collogues
still refused to believe it).
The Internet has proved successful because it had a cultural context to complement usable technology. Not only did it provide a way to communicate, but reasons why you might communicate and what was considered good and bad communication behaviour.

 The Internet represents a huge marketplace of technology
ideas. Researchers develop technologies which could be used as part of the
Internet, but then it is up to their peers and then the general public, to
decide if these technologies will be used. Sometimes an old technology is
dusted off and given new life, when the need arises.
The Internet represents a huge marketplace of technology
ideas. Researchers develop technologies which could be used as part of the
Internet, but then it is up to their peers and then the general public, to
decide if these technologies will be used. Sometimes an old technology is
dusted off and given new life, when the need arises.
As a result the Internet is remarkably robust and adaptable. When there is a problem, or an opportunity, technologies and social practices are invented or adapted to meet the challenge. Some of the process is by natural selection, where many ideas are tried and on turns out to work. In other cases there is a preplanned political process, much like that used outside cyberspace, where people campaign for different approaches.
11 September 2001
The Public Affairs Division of the Australian National University contacted me on the day after the attacks on the World Trade Centre and the Pentagon. The university was receiving a large number of calls from the media asking for expert opinion. One aspect of the disaster was the effect the loss of computer and telecommunications facilities and the effect on the functioning of world communications and commerce. In response I established aweb page with what information was available and issued an on-line request to my colleagues for information.
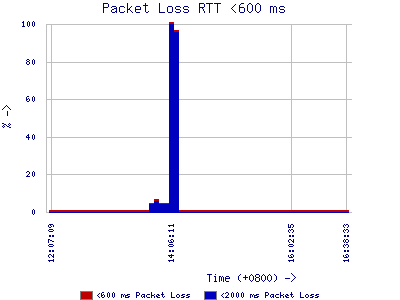
It quickly became clear that the Internet was operating globally much as usual. In dozens of press and radio interviews over the following days I had to explain that the Internet had not stopped working. The web basedInternet Weather Report indicated some delays in theNorth East of the USA.Statistics from theAustralian Academic and Research Network and theInternet Average showed a sharp spike in packet loss (a measure of network load) for a few minutes, at the time the southern tower of the World Trade Centre collapsed. Far worse problems have been caused to the Internet by viruses and oceanic cable breaks.
Many of theWeb linked Cameras of the New York City Department of Transportation Advanced Traveler Information System (ATIS) were still functioning the following day. These camera are designed to show traffic conditions and allowed anyone on the net to see rescue operations underway.
Web sites of major news organisations quickly became heavily loaded. Some organisations made rapid and changes to the sites, paring back graphics and fancy features to handle more basic requests for information.
Public discussion groups for sharing information on the attack quickly sprang up. Amoderated e-mail list to collect first person accounts by those directly impacted was created. The University of Sydney - Department of Civil Engineering provided a web page withengineering aspects, of the World Trade Centre. These sites were remarkable, not only for how rapidly they were created, but the depth and credibility of the information.
From:The Internet and the US Attacks, Tom Worthington, ABC's Public Record, 28 September 2001
... TheInternet Average indicated a sharp increase in packet loss at 14:00 GMT September 11...
The Australian Academic and Research Network (AARNet)statistics , packet loss on its MCI (San Francisco) link went from zero to 4% at 13:39:25 GMT, then to 100% at 14:06:11 GMT, 96% at 14:07:48 GMT and then zero again at 14:29:07 GMT. According to the ABC Radiotimeline, this is the time the southern tower of the World Trade Center collapsed.
From:IT issues and Internet Resources Related to the US Disaster, 12 September 2001
11 September 2001
The Internet survived the attacks and provided a useful public service. The massive wave of cyber-attacks predicted by some commentators did not happen. So what happened and what could have been done better?
One immediate reaction by some web sites was to simplify their designs to better handle peak loads. Web masters stripped unnecessary images and navigation features from their home pages to allow millions of "hits" on the sites. This was done in a haphazard way and for only a few days after 11 September. But there is actually a systematic way to do this, carefully designed into the web.
Accessible web site design can adapt automatically to available network capacity. Under normal conditions a full web display is presented with lots of images, navigation features and animation. If the web server becomes overloaded, the network congested or the user has a limited function web device, the extra features can be dropped leaving a simple, efficient design. In an emergency the user can be automatically presented with a simple text-only page a fraction the communications cost of the full version.
Accessible web design was developed for disabled people, including the blind, to be able to use the web, as well as make it more flexible for others. ANU IT students learn how to design web pages which offer a low bandwidth option without large images for mobile web users, using the same techniques as for the blind. Unfortunately most web designers ignore the needs of their less network equipped customers and their legal obligations to the disabled and create inflexible, resource hungry sites.
A wave of terrorist cyber-attacks may have actually have happened, but not been noticed. Since the earliest days of the Internet it has been subject to security attacks. In response an infrastructure has grown up to detect attacks and help defeat them. In Australian this effort is headed by AusCERT and world wide by CERT. These organisations collect reports of Internet vulnerabilities and distribute warnings. In effect this is the Internet equivalent of neighborhood watch. Very occasionally a problem comes to public attention, but most of the time problems are routinely dealt with. There are many thousands of system attacks every day, most by script kiddies (naive hackers using attack programs they got from someone else and don;t understand). In an environment where attacks are constant and nay
The convergence of the Internet and broadcasting also offers the possibility of blending the best features of both. This is an areas where more research is required. However, a recent announcement by Microsoft that they will support TV, may spur commercial work. The ANU Department of Computer Science happens to be one of the centers of expertise in this field in Australia. This could offer a way out of the digital TV and Pay TV policy problems currently troubling the federal government.
Web Services Security Risk
While the Internet has coped well with security attacks, we should not be complacent. A major developing risk is the new technology of web services. Web Services does for electronic transactions, what the web did for electronic documents: make them easy to create and link together. However, security is an optional component of web services. We need specialized "proxy servers" which check the transactions going in and out of the organisation through their firewall.
If you want to know more about the web services and its data management implications, then you will have to buy the very expensive industry report I preparing on the subject, or enrole in the ANU course where you can get the same content much cheaper. ;-)
About The Speaker
 Tom Worthington is an independent
information
technology consultant and author of the book
Net
Traveller. Tom is one of the architects of the
Commonwealth Government's Internet and web strategy. The first Web Master for
the Australian Department of Defence, in 1999 he was elected a Fellow of the
Australian Computer Society for his contribution to the development of
public Internet policy. Tom lectures on electronic commerce and web
technology at the Australian National University and is a Visiting Fellow in
the Department of Computer Science. He is a director and a past President of
the Australian
Computer Society, a member of the Institute of Electrical
and Electronics Engineers and the Association for Computing
Machinery.
Tom Worthington is an independent
information
technology consultant and author of the book
Net
Traveller. Tom is one of the architects of the
Commonwealth Government's Internet and web strategy. The first Web Master for
the Australian Department of Defence, in 1999 he was elected a Fellow of the
Australian Computer Society for his contribution to the development of
public Internet policy. Tom lectures on electronic commerce and web
technology at the Australian National University and is a Visiting Fellow in
the Department of Computer Science. He is a director and a past President of
the Australian
Computer Society, a member of the Institute of Electrical
and Electronics Engineers and the Association for Computing
Machinery.
Further Information
The Internet and the US Attacks, ABC's Public Record, 28 September 2001
IT issues and Internet Resources Related to the US Disaster, 12 September 2001
- Net terror fails to live up to hype, Simon Hayes, The Australian, SEPTEMBER 10, 2002
A Common Understanding: Metadata, Data Management, the Digital Library and Electronic Document Management, For: Computing 3410 Students, The Australian National University
Author's home page
Comments and corrections to: webmaster@tomw.net.au
Copyright © Tom Worthington. 2002