Workshop: B2B-or-not-B2B? IT Strategies for Surviving Recession
by Tom Worthington FACS
6 to 8 July 2001, Hyatt Regency, Coolum, Australia
For the Third Australian IT Directors' Summit
Some books: Buying and selling on the Internet
Many IT Directors have only known times of expansion and plenty in business. What strategies are needed to cope with recession? Organisations are reconsidering expenditure on IT, with the collapse of the DOT.COM companies. Tom Worthington argues that IT managers should not give up on the Internet and the web. Low cost "make do" strategies re-using existing hardware and low cost software may not be glamorous, but may save your job. The workshop will use a live Internet connection to explore issues raised by participants.
Some issues:
- Investing in staff training to lower costs.
- Using the Internet to save money, but look hi-tech.
- Revitalising old hardware.
- Open source software to save money.
- Expanding IT to other corporate areas and spend their budget.
Introduction
This seminar is modified from one prepared for small business and sponsored by the Federal Government's Business Entry Point. The central point of the presentation is that simple and inexpensive IT techniques which small business can afford to implement can also help big business. Large organisations tend to assume they need large and complex systems. But simple systems can give a quick return on investment.
The seminar will look in more detail at the issues of wireless and B2B touched on briefly in the Keynote: Exploring Australia's IT Landscape.
Using the Internet to save money, but look hi-tech
Delivery of services via the Internet
Where a service is delivered via telecommunications, the outsourcing of the function can be facilitated. It should be noted that this only indicates that outsourcing is made possible; if it should be carried out is a wider question.
When a service is made available by phone or on-line, all the client knows is what they hear, or see on the screen. This flexibility is one reason why on-line services need special security features, such as Public Key Authentication.
An on-line service could be moved from an in-house network to an outsourced service provider. Alternatively the system could remain in-house, while the service and support of the information on the system was outsourced, or both the system and support could be moved.
To facilitate outsourcing each service would need to have a separate identity, such as a set of web pages and e-mail addresses. With this in mind, organisations might want to keep separate there general web sites and service delivery sites.
Internal communication and information can now be provided using internet technology on an internal corporate network commonly called an "intranet". There is nothing magical or special about an intranet, its just a bit of the Internet which has been cut of from the rest of the world, or hidden behind a firewall. The services could have been provided by any one of a number of technologies over the last 10 years. The Internet has just popularized, standardized and lowered the cost of what IT professionals have been trying to do for years.
While the Internet may provide the tools for on-line business, people may not necessarily know how to use them for business. The problem is to get staff to take the Internet seriously as a business tool. Staff have to have the security issues of the 'net explained to them. Backup and security of information is important.
Wireless
The potential of wireless Internet, is yet to be realized. Wireless Application Protocol (WAP) has turned into another dot.COM pipe dream. IT directors need to consider a broader wireless strategy. Recent developments with wireless standards and equipment mean that this may be incorporated into the organisation's main web strategy. The result will be an overall lower cost and complexity.For first semester 2001 I have been teaching information technology students at the Australian National University about wireless technology and web site design. This rather academic work has had a remarkable, commercially valuable spinoff. It appears that a viable wireless strategy is to design web pages which implement accessibility guidelines for the disabled and are design to display on a one quarter VGA screen. Organisations which accept these limitations on the design of their web sites will be able to deploy to a new range of hand-held devices implementing web browsers and GPRS, with no extra investment being required.
Up until a few months ago most commentators agreed that WAP (Wireless Application Protocol) devices would be the next communications revolution. However, that has now changed and WAP is essentially dead as a product. Organisations which have implemented WAP have wasted their money, as have mobile telephone handset companies and telcos investing in WAP and 3G spectrum.
WAP came from the mobile telephone industry: mobile telephone handsets had computing capacity added, to become wireless data devices. We may see a rapid development of a wireless Internet approach from the computer industry: hand held computers will have wireless communications added to become multi-function phones. The General Packet Radio Service (GPRS) option being added to existing GSM mobile networks will provide most of the functionality of the planned 3rd generation high speed networks at far lower cost.
Wireless Application Protocol (WAP)

- What is WAP?
- The Wireless Application Protocol (WAP) is an open, global specification that empowers mobile users with wireless devices to easily access and interact with information and services instantly...
- What type of devices will use WAP?
- Handheld digital wireless devices such as mobile phones, pagers, two-way radios, smartphones and communicators -- from low-end to high-end.
From WHAT IS WAP AND WAP FORUM?, Wireless Application Protocol Forum Ltd, 2001
- Which wireless networks does WAP work with?
- WAP is designed to work with most wireless networks such as CDPD, CDMA, GSM, PDC, PHS, TDMA, FLEX, ReFLEX, iDEN, TETRA, DECT, DataTAC, Mobitex.
- What operating systems are compatible with WAP?
- WAP is a communications protocol and application environment. It can be built on any operating system including PalmOS, EPOC, Windows CE, FLEXOS, OS/9, JavaOS etc. It provides service interoperability even between different device families.
As currently conceived WAP is unlikely to become the mainstream technology for wireless Internet applications. The limitations of current WAP devices require content to be specially designed in the Wireless Markup Language ( WML).
WML is defined using the Extensible Markup Language (XML), which is being promoted for new web content. This code will actually run on most modern web browsers, although the formatting may look a little odd on a larger screen than it was design for.
WAP has been designed to fit within the limitations of a low speed (9600bps or slower) dial-up mobile telephone link and a low capacity hand held client device. The result is a set of specifications which follow Internet standards as much as possible and meet the limitations set for them. The result is an additional set of standards, different to existing Internet and web use.
I-mode
I-mode provides a different, and more promising approach to a web service on a hand held device. I-mode uses a proprietary mark-up language based on HTML:
First introduced in Japan in February 1999 by NTT DoCoMo, i-mode is one of the world's most successful services offering wireless web browsing and e-mail from mobile phones. Whereas until recently, mobile phones were used mostly for making and receiving voice calls, i-mode phones allow users also to use their handsets to access various information services and communicate via email.In Japan, i-mode is most popular among young users, 24 to 35 years of age. The heaviest users of i-mode are women in their late 20s. As of November 2000, i-mode had an estimated 14.9 million users.
When using i-mode services, you do not pay for the time you are connected to a website or service, but are charged only according to the volume of data transmitted. That means that you can stay connected to a single website for hours without paying anything, as long as no data is transmitted.
From I-mode FAQ, WestCyber Corporation, 2000 (no longer on-line)
W3C is also working on adapting standard HTML for mobile devices, to provide a less proprietary approach:
A new class of electronics devices with Internet access capability called "Information Appliances" was recently born. This Internet access capability is embedded in devices such as televisions, set top boxes, home game machines, telephone-based terminals, PDAs, car navigation systems and cellular phones. These Internet appliances will drive the merger of wireless and wired Internet world that will eventually create a much larger industry than today's predominantly wired Internet industry.From HTML 4.0 Guidelines for Mobile Access, W3C Note, 15 March 1999
It may be some years (or never) before a suitable standard for mobile devices is adopted. An alternative approach by the CSIRO, is to render the web content in a format to suit the display device:
Combining XML, ASP and database technology provides a powerful mechanism for the development of mobile applications. We describe the development of an application that provides name, rank and phone number information for an organization. The information is accessible from a web browser or a WAP browser on a mobile phone. It uses ASP scripting to query a database and build an XML document satisfying the search criteria. We’ll detect the browser type then apply an XSLT style sheet to format the information for display on the detected device. A generic windows scripting component (WSC) derived from that described by Mike D. Jones in a February 7 2000 Active Server Developers Journal article is used to query the database and return the result to an ASP script as an XML document. You can view a working copy of the application at http://mobile.act.cmis.csiro.au and download the files to implement the applicationFrom "XML and Mobile Computing", Paper and Demonstration, by Ken Taylor, CSIRO Spatial Information Systems Group.
 But a much simpler approach may be possible: Build web
pages which work well on conventional web browsers and on hand held devices,
without the need for changes. While this wouldn't be feasible with today's WAP
phones, it is possible with the new range of PDA mobile telephones. These have
a quarter VGA (320 x 240 pixels) colour or monochrome screen and a cut down
web browser and GPRS data access to the Internet at speed comparable to a slow
dial-up line.
But a much simpler approach may be possible: Build web
pages which work well on conventional web browsers and on hand held devices,
without the need for changes. While this wouldn't be feasible with today's WAP
phones, it is possible with the new range of PDA mobile telephones. These have
a quarter VGA (320 x 240 pixels) colour or monochrome screen and a cut down
web browser and GPRS data access to the Internet at speed comparable to a slow
dial-up line.
The limitations of small screen size, limited keyboard and lower bandwidth connection can be overcome by using accessibility features originally designed for the disabled.
Accessibility for the disabled
Web accessibility guidelines have been developed to assist designers to make web sites which can be used by the greatest range of people. The most respected guidelines are those from the World Wide Web Consortium. Last year I used those guidelines to assess accessibility for the blind to the SOCOG Sydney Olympic Web site, in a case before the Human Rights and Equal Opportunity Commission.
There is a common misconception that accessibility issues are exclusively to do with a small section of the community who have physical disabilities. However, as the W3C guidelines make clear, they can provide benefits to the wider community:
For those unfamiliar with accessibility issues pertaining to Web page design, consider that many users may be operating in contexts very different from your own:
-
They may not be able to see, hear, move, or may not be able to process some types of information easily or at all.
-
They may have difficulty reading or comprehending text.
-
They may not have or be able to use a keyboard or mouse.
-
They may have a text-only screen, a small screen, or a slow Internet connection.
-
They may not speak or understand fluently the language in which the document is written.
-
They may be in a situation where their eyes, ears, or hands are busy or interfered with (e.g., driving to work, working in a loud environment, etc.).
-
They may have an early version of a browser, a different browser entirely, a voice browser, or a different operating system.
Content developers must consider these different situations during page design. While there are several situations to consider, each accessible design choice generally benefits several disability groups at once and the Web community as a whole. For example, by using style sheets to control font styles and eliminating the FONT element, HTML authors will have more control over their pages, make those pages more accessible to people with low vision, and by sharing the style sheets, will often shorten page download times for all users.
From Recommendation Web Content Accessibility Guidelines 1.0, World Wide Web Consortium, 5-May-1999.
These issues are particularly relevant to wireless mobile devices. A hand held device may be used in a situation where it is difficult to see or hear, where the user's hands are needed for other tasks or where they are distracted. These devices tend to have small screens, limited graphics, limited keyboards and pointing devices. The wireless connection makes the connection slow and the device may have a less capable browser. In effect the user of the handheld device suffers a temporary disability which can be overcome by applying the guidelines.
Examples of use of wireless devices in motion
... Gus' Cafe was opened by Augustin "Gus" Petersilka, advocate of the outdoor Viennese cafe. ... Well after Gus' time the cafe has changed from using pencils and note paper for taking orders and now has wireless PDAs. The staff were a bit busy taking orders to stop and explain the system to me, but it appears to use standard Palm III personal digital assistants (PDAs) for taking the orders.
From Networking at Gus' Cafe, 26 January 2001
... visit Philippe Quéau Director of Information Society Division UNESCO. This was a good excuse to try the Eurostar train through the Channel Tunnel from London to Paris .... Mobiles don't work during Channel Tunnel transit (20 minutes) and in shorter tunnels en-route (mostly in the UK). I noticed that phones do work in the London Underground. As soon as we existed the tunnel in France, I received a message on the phone from SFR welcoming me to their mobile service, which is a nice touch. I uploaded the first draft of this web site, using an GSM infrared interface. This was only just done when the battery went flat in my computer...
From London to Paris By Eurostar, 19 October 2000
Accessibility and I-mode
I-mode uses a subset of HTML, so that I-mode pages are upward-compatible with conventional web browsers:
3.2 Features of Compact HTML
The Compact HTML is a subset of HTML 2.0, HTML 3.2 and HTML 4.0. We describe the major features which are excluded from Compact HTML, as follows.We define that Compact HTML includes GIF image support...
- JPEG image
- Table
- Image map
- Multiple character fonts and styles
- Background color and image
- Frame
- Style sheet
More complex web sites can be constructed from simpler i-mode pages.China Urges Advanced Countries to Help Developing
A Chinese central bank official on Sunday urged advanced countries to coordinate their macroeconomic policies and keep the major currencies' exchange rates stable to create an environment conductive to stability and growth for developing countries.
(04.30 14:0)
Top of Group Top Page
B2W: Business2Where?
After the disappointment of B2C and B2B, there is a future for e-commerce. However, grand strategies of global market dominance through exciting B2x strategies needs to be abandoned. E-commerce can provide significant cost savings using simple technology which is an extension of conventional business practice.
IT professionals have developed many powerful techniques for the analysis of business problems. Just as business people seemed have forgotten their financial skills when investing in Internet projects, IT people seem to have forgotten all the techniques of good IT design when building web applications.
Graphic designers and marketers should be kept away from the design of serious e-commerce web sites. What is needed are analysis and design techniques from IT traditions but adapted to the web. One attempt to do this is WebML.
Web Modeling Language (WebML) is a notation for specifying complex Web sites at the conceptual level. WebML enables the high-level description of a Web site along multiple dimensions:From "Modeling the CDNOW Web site" by Aldo Bongio (ZIPped PPS, 323 Kb; PowerPoint Viewer required) (Ceri et al 2000).
- its data content (structural model),
- the pages that compose it (composition model),
- the topology of links between pages (navigation model),
- the layout and graphic requirements for page rendering (presentation model),
- and the customization features for one-to-one content delivery (personalization model).

Example of structure schema represented in an Entity-Relationship Diagram

Excerpt from a site view defined in WebML
Design Process in WebML
- The data expert designs the structural model.
- The application architect designs the pages and navigation between pages.
- The style architect designs the presentation styles of pages.
- The site administrator designs users and personalization options, including business rules, and is responsible of site publishing and evolution.
WebML Design Process
From: WebML in a Nutshell, WebML.org, 2001
B2G Director for Australia: A candidate for Analysis
The Department of Employment, Workplace Relations and Small Business (DEWRSB) has issued a Request for Expressions of Interest to assist with an e-commerce initiative in the business-to-business and government-to-business environments :
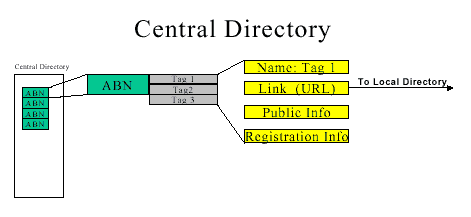
The aim of the initiative is to build a high level electronic directory, in an electronically open and commercially neutral environment. This directory will service national requirements by providing a high quality unique electronic identification and authentication directory.
Power of the Directory
This directory will be designed to engender confidence and trust in the online business environment. A registration process will protect:
From: ( EOI2001/10, 2001)
- The brand.
- Intellectual property.
- Terms of trade of electronically based products and services.
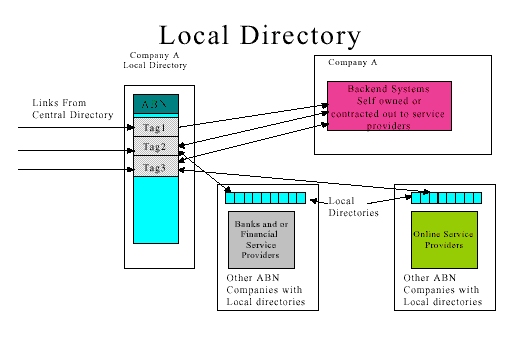
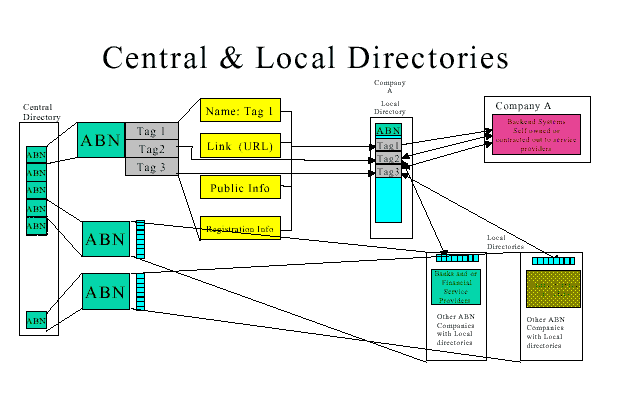
The initiative is generally seen as having a Central Directory containing ABNs and there associated tags and a Local Directory for each ABN that is actively using the Central Directory. The Local Directory, identified by its ABN will be the interaction entry point for each of the interaction made available by the business entity. Although each business entity will require a Local Directory it is envisaged that the Local Directory would be most likely be hosted by an intermediary such as an ISP and offered to individual business entities as a value added service. Businesses would access and manage their Local Directory remotely using strong authentication facilitated by a Public Key Infrastructure.
From: ( EOI2001/10, 2001)
This is better explained in several diagrams provided by DEWRSB. The diagrams could be used to implement the WebML process for formal design of the web site, to provide a systematic approach to implementing the system. Such a system could be expected to have a high transaction rate and require careful optimization of the implementation, which would be aided by formal analysis of the data structures. An accessible design, implementing the W3C guidelines, would minimize network load as well as providing for the wide range of users of the system. A wireless design might be of value for small businesses using hand held and appliance web terminals in place of conventional PCs.
Central Directory
Local Directory
Central & Local Directories
PKI: What Not to Invest In
While the Federal Government and Banks are painting a positive picture of digital certificates:
Government to accept bank digital identity certificates - The Minister for Communications, Information Technology and the Arts, Senator Richard Alston, today announced that digital signature certificates issued by Australian banks to businesses will be accepted by government agencies. For more info see the Project Angus - ABN-DSC FAQ.NOIE Web Site 22/03/01
Check there is a real business case for them before implementation in your organisation.
Although the Australian Government's Gatekeeper initiative to implement PKI (Public Key Infrastructure) technology for electronic transactions was established just over three years ago, there hasn't been much headway in seeing its acceptance in the wider business community. ZDNET
Use relevant service rather than doing it yourself:
Is Your Data Taking the Scenic Route? By Dylan Tweney, May 24, 2001: If you think your website is running too slowly, it could be a problem with your ISP. Here's why. Ever notice how fast some sites come up in your browser -- say, Yahoo, for instance? That's not just because the site has powerful servers (although it does) or because it's a text-heavy page with only a few, small graphics (although it is). One key ingredient of Yahoo's speed is that its servers have long been hosted by a company -- GlobalCenter, now part of Exodus Communications -- that has excellent data-sharing arrangements with other ISPs. Because of these so-called peering agreements, Yahoo's pages take the express route from their servers to your browser. Your site's pages, by contrast, are probably taking the scenic route...
Look at cooperating as the researchers are doing:
AARNet prepares to interconnect to Internet2 AARNet has acquired a "3-drop ring" on the Southern Cross Cable Network (SCCN) and will use this capacity to interconnect to the overseas advanced research and education networks. AARNet's drop-points on SCCN are Sydney, Kahe Point (Oahu, Hawaii), and Hillsboro (Oregon, USA). From Hillsboro, AARNet has arranged to backhaul this capacity to the Pacific NorthwestGigaPoP(PNWGP) in Seattle (PNWGP) ... AARNet will participate in theInternational Transit Network (ITN) making 24 other regional and national advancedresearch and education networks available...From: AARNet News 28-05-2001
See what results are coming from advanced networks:
A national advanced network backbone and a world-leading broadband wireless project will receive over $37 million in Government funding, leveraged by another $93 million contribution from consortium members, under the Advanced Network Program, the Minister for Communications, Information Technology and the Arts, Senator Richard Alston announced today. DCITA Media Release 29 May 2001
last
One of the jokes of the IT industry is the "paperless office". By now everyone was supposed to be using electronic communications and so paper would be obsolete in the office. The opposite has happened with more paper being used with laser printers and word processors. However, this can combatted in organisations. Adopt a "paper last" policy: use paper, but only as the last step in a process and only where it is really needed. As well as saving on the cost of paper, printing and postage, this saves on storage and handling of documents. It may also save on installed an expensive and complex electronic document management system.
E-mail can be used for routine business correspondence. Encourage staff to include the e-mail address on all correspondence. Ask organisations you do business with for their e-mail addresses. Provide brochures via the web or by e-mail. Explain that you accept orders by e-mail and prefer to send invoices by e-mail.However, you need to train your staff on How to Read and Write E-mail Messages.
Date: in the, 23 Mar 2001 20:47:41 +1100 (EST)
From: porders@xxxxxx.com.au
Please process the following orders.
PLEASE
* quote our order number on the invoice
* quote our order number on correspondence
* backorder and notify us if unavailable
* send the exact format requested
* supply the latest edition unless otherwise indicated
FOR AUSTRALIAN SUPPLIERS ONLY
-----------------------------
* If an ABN is not evident on your Tax Invoice when
* supplying goods, or you are unable to prove exemption,
* 48.5% of the Invoice value will be deducted from your payment
as per ATO requirement
* Our ABN is xx xxx xxx xxx.
---------------------------- O R D E R ----------------------------
xxxxxx PTY. LTD. ABN xx xxx xxx xxx, ACN xxx xxx xxx x
xxxxx ST, xxxx NSW 2xxx
TEL: +61 x xxxx xxxx FAX: +61 x xxxx xxxx
xx MAR 01 ORDER NO. Txxxx
TOMW COMMUNICATION PTY LTD
PO BOX 13
BELCONNEN ACT 2617
Supplier code: xxxxx
ISBN Qty Title & Author
-- ------------------------------------------------------------ ----
0646391593 1 Universal service?: telecommunications policy in
Australia and people with disabilities (Paperback)
Bourk, Michael J. & Worthington, Tom
It should be noted that there is no fancy formatting in the order, just text.There is no need for a complex "middleware" application to generate such orders. A small modification to the same system which prints paper orders is all that is required.
Paper-last invoices
Send your clients e-mail invoices as the first step. This can be a simple text-only e-mail message:
Date: Tue, 03 Oct 2000 09:11:24 +1000
To: "xxxx" <xxxx@xxxx.com.au>
From: Tom Worthington <tom.worthington@tomw.net.au>
Subject: xxxxxx - Invoice for xxxx
TAX INVOICE - TOMW COMMUNICATIONS PTY LTD - ABN: 17 088 714 309
Invoice number: 2000-xx
Date: x October 2000
FROM: Tomw Communications Pty Ltd
PO Box 13, Belconnen ACT 2617, Australia
A.C.N. 088 714 309 http://www.tomw.net.au
e-mail: accounts@tomw.net.au
ph: 0419 496 150
fax: 02 6262 7954
TO: xxxxxxxx
xxxxxxxxx
xxxxxxx
Att: xxxxx
FOR: xxxxxxxxxxxxx
Price: $xx,xxx.00
GST: $x,xxx.00
---------
Total including GST: $xx,xxx.00
=========
Terms: 14 days
Payment to:
Account Name: TOMW COMMUNICATIONS PTY LTD
Bank: xxxxx
BSB Number: xxxxxx
Account Number: xxxxxx
Or cheque payable to:
Tomw Communications Pty Ltd
This invoice was generated manually, as my consulting company only sends a handful of orders a year. However, an automated system can be modified to produce such orders.
Some organisations don't like plain text invoices, but will accept an "electronic" formatted one. In that case you can generate a word processing file which will produce something which looks just like an invoice when printed. Attached to an e-mail message this is cheap and easy to send. The recipient pays the cost of printing the invoice, if required. If that isn't acceptable, you can send them the same document via a fax interface.
There are some standards in use, and many proposed, for handling electronic orders and invoices automatically. While these look high-tech, underneath they use simple text formats and so you do not necessarily need highly complex software to process the formats. If you are a member of an industry which requires use of a particular set of formats, check if there is a free or low cost version of the software to handle them, before purchasing a fully fledged e-commerce system. If your organisation has a recent graduate in IT, you may find they already know how to program e-commerce interfaces.
Simple Low Cost Electronic Payment
If your company deals with retail consumers for small value transactions, then you might have to take credit cards. However, if you deal with other companies (so called B2B or "Business to Business" e-commerce), then credit cards may be an unnecessary expense. Credit cards incur significant fees and are not suitable for most B2B e-commerce.
One problem with this system is that it can be difficult to know who the money came from (the so called "Eighteen Character Problem". Systems such as the BPAY electronic bill payment service offered by a number of financial institutions, use check digits to provide better payment tracking information. However, merchants must register for BPAY, it may incur an additional charge and require more complex software. One way around this is that some banks issue all accounts with BPAY facilities automatically for free, allowing its use by individuals. This might be usable for some smaller businesses.
If your company does sell consumer items then the general public will expect to be able to pay by credit card. There are fully automated on-line credit card systems available. However, you should consider one low cost simpler alternatives first:
Researching On-line
Staff can use the Internet as a low cost research tool to find out about individuals, organisations and products. A lot of more expensive and time consuming processes can be saved by simple on-line checks.
Company registration
The Australian Securities and Investments Commission provide a free index of corporate and business names which can be searched via the web. This finds company and business names registered across Australia.
A search on "tomw" finds:
| 2 names found (* indicates former name) | ||
| Number | Status | Name |
| ACT F 00091941 | REGD | TOMW COMMUNICATIONS |
| ACN 088 714 309 | REGD | TOMW COMMUNICATIONS PTY LTD |
Selecting the first entry shows a business name:
Extracted from ASIC's database at 09:31:51 on 19/04/2001
Name TOMW COMMUNICATIONS ACT
F 00091941 Type Business Names Registration
Date28/01/1999 Status Registered Principal
Place of
Businessnot available Jurisdiction Registrar-General's Office, ACT
The second:
Extracted from ASIC's database at 09:30:55 on 19/04/2001
Name TOMW COMMUNICATIONS PTY LTD ACN
088 714 309 ABN
17 088 714 309 Type Australian Proprietary Company, Limited By Shares Registration
Date20/07/1999 Status Registered Locality
of Registered
OfficeCanberra ACT 2600 Jurisdiction Australian Securities & Investments Commission
These are the documents most recently received by ASIC from this organisation. Page numbers are shown if processing is complete and the document is available for purchase. Received Number Pages Description 18/12/2000 08871430K 3 316 (AR 2000) Annual Return Change to Principal Place of Business
316P Change of Name or Address of Officeholder 316L Annual Return - Proprietary Company 15/12/1999 08871430J 3 316L (AR 1999) Annual Return - Proprietary Company
20/07/1999 0E3263651 3 201C Application For Registration as a Proprietary Company
Further information is available by paying a fee to an ASIC information broker on-line, but this is enough to see that the information is at least consistent with what is on the company web site.
Web registration
Web addresses are registered in a global database. This includes names and contact details. For tomw.net.au the details are:
Name Status Report
Name: tomw.net.au
This name is configured in the DNS:
Name Servers:
tomw.net.au name server oldent.powerup.com.au tomw.net.au name server galileo.powerup.com.au
Mail Servers:
tomw.net.au mail is handled (pri=10) by mail.tomw.net.au tomw.net.au mail is handled (pri=50) by horizon.webcentral.com.au tomw.net.au mail is handled (pri=100) by enterprise.powerup.com.au
SOA record:
tomw.net.au start of authorityenterprise.powerup.com.au
domain.webcentral.com.au( 2001031614;serial (version) 900;refresh period 300;retry refresh this often 86410;expiration period 86400;minimum TTL )
tomw.net.au is not in the AUNIC registry.
Querying whois.connect.com.au:
% RIPEdb(3.0.0b1) with ISI/Qwest RPSL extensions
domain: tomw.net.au
descr: Tomw Communications (ACN: F 00091941)
PO Box 13
Belconnen ACT 2617
admin-c: TW31-CC-AU
tech-c: JA1-AU
zone-c: JA1-AU
nserver: galileo.powerup.com.au
nserver: oldent.powerup.com.au
notify: dbmon@connect.com.au
changed: net-au-admin@connect.com.au 19990222
source: CCAIR
person: Tom Worthington
address: Tomw Communications
address: PO Box 13
address: Belconnen ACT 2617
phone: +61 419 496 150
nic-hdl: TW31-CC-AU
notify: dbmon@connect.com.au
changed: net-au-admin@connect.com.au 19990222
source: CCAIR
% referto: whois -h whois.aunic.net -p 43 -s AUNIC -T person,role JA1-AU
Administrator of parent domain net.au is net-au-admin@connect.com.au.
The phone book
The White Pages for Australia can be searched on-line.
The web
Search engines can be used to look for company and personal names, as well as addresses, phone and fax numbers listed in web pages. This finds not only web pages provided by a company, but also entries from the media and other organisations about the company. A search for "Tomw Communications" finds almost 200 entries, a few of which are:
TomW Communications
Tomw Communications Pty Ltd. TomW Communications was ... 1
August 1999. TomW Communications Pty Ltd. ...
www.tomw.net.au/admin/ - 4kTomW Communications Pty Ltd - Media Releases
www.tomw.net.au Tomw Communications Pty Ltd - Media Releases. ... Web page by Tomw
Communications Pty Ltd ACN 088 714 309 - Comments to: webmaster@tomw.net.au.
www.tomw.net.au/media/ - 3k[SLUG] [LINK] Microsoft Windows to disappear within two years ...
... two years, Media Release . Tomw Communications Pty Ltd - Media Release Microsoft
Windows to disappear within two years - Says Cyber Sooth Sayer http://www.tomw ...
www.slug.org.au/lists/archives/slug/2000/May/msg00864.html - 9k -Newsgate: uk.transport.buses: Drive double-decker bus for the ...
... tomw.net.au/nt/uk.html -- Tom Worthington FACS tom.worthington@tomw.net.au Director,
Tomw Communications Pty Ltd ABN: 17 088 714 309 http://www.tomw.net.au PO ...
www.newsgate.co.uk/uk/uk.transport.buses/msg05802.html - 6kI-cubed Web Accessibility Summit 2000
... 10.05am - 10.35am Morning Tea. 10.35am - 11.25am Tom Worthington, Director
Tomw Communications Olympic Failure: A case for making the Web Accessible. ...
www.webaccess.iii.rmit.edu.au/program.html - 6kThe University of Melbourne Library - Giblin Economics and ...
... MICHAEL J BOURK ; EDITIED [SIC.] BY TOM WORTHINGTON. Belconnen, ACT : TomW Communications,
2000. 384.0994 BOUR. TELEVISION, NATION, AND CULTURE IN INDONESIA ...
www.lib.unimelb.edu.au/collections/ecocom/newbookslist.html - 25k
Don't Waste Money on Computer Technology
While computers and telecommunications (called collectively "Information technology" or IT) can enhance business processes, they have to pay their way. Many in business assume that using a computer or the Internet will automatically make their business more efficient; it will not. What buying IT will do first of all is increase costs. Before spending on IT you must make a business case that it will either reduce costs overall or increase revenue. Also you must asses that the risks involved are acceptable. Many, perhaps most, IT projects fail and produce no benefit to the organisation at all.
e-mail lists
A simple and effective way to keep in contact with staff, clients and other interested parties is with e-mail lists. Effective use of lists is made by the Australian Computer Society. There is specialized software which large organisations install on their own Internet servers and some ISPs provide lists as part of a web service, however, the ACS uses the free advertising supported list service Yahoo! Groups. This service provides for closed groups (by invitation only) and lists where only you can post comments. An archive off all messages posted can automatically be kept and subscribers can be prevented from sending large attachments to messages. Using a list can save on sending out routine material by mail or fax and save maintaining subscription lists.
Internet-lite
You can minimize Internet costs and make it more business-like by switching off many of the fancy features. Where remote mail clients are being used, setting the default on e-mail programs to only download the first 50 kbytes of each message may reduce the load on internal networks. If the rest of a particular message is really wanted it can be requested.
An aggressive caching strategy can be used to cut down external and internal network traffic. Web browsers can be set to never check for newer versions of stored pages. The browser will download each page only once and keep a copy of it in cache. Staff will need to be trained to use "refresh" to get updates.
Web pages can be designed which drastically cut down on network and server resources. This can be used to create very simple web pages for internal staff where market image is less of an issue. This can also be used to create simple web pages for clients. Rather than this being see as cost cutting, it can be a marketing plus if explained as providing access to the disabled or wireless ready web access.
Invest in Training First
The computers and networks used by successful and unsuccessful businesses are much the same. The difference is the level of expertise available to exploit the technology. The best investment to make is in training.
Don't Overinvest
New software takes effort to learn and new hardware time to install. Are more powerful, more expensive PCs really needed every 18 months to run your business?
Works suites: Look at alternatives to big brand name packages. A suite of "works" software: word processor, spreadsheet and simple database probably will do for many staff. As well as saving money the simplified packages are easier to use, because they do less.
Free readers: Major software companies, provide free viewer programs over the Internet for reading files from their packages. As well as being free these programs are much smaller than the full editing packages requiring fewer system resources. Also because of their limited function they are less susceptible to virus attack.
Don't upgrade: The latest version of a software package is unlikely to significantly improve your business profitability. Installing the package, learning to work it and dealing with all the problems it causes on your company will distract staff from running the business.
Do you need PCs at all?: Graphics terminals using a shared, centrally managed system, such as those from Citrix is a viable option for many situations.
Don't Buy a Big Network
Access to the Internet is a very useful business tool. The Internet was designed as a heterogeneous ad-hoc fault tolerant network. That means just about any brand of computer will do, you don't necessarily need a full time dedicated network.
 Tom Worthington is a Visiting Fellow in the
Department of Computer Science at the Australian National University. He is an
independent electronic business consultant and author of the book Net
Traveller. Tom is one of the architects of the Commonwealth Government's
Internet and web strategy. The first Web Master for the Australian Department
of Defence, in 1999 he was elected a Fellow of the Australian Computer Society
for his contribution to the development of public Internet policy. Tom is a
director and past President of the Australian Computer Society and a voting
member of the Association for Computing Machinery.
Tom Worthington is a Visiting Fellow in the
Department of Computer Science at the Australian National University. He is an
independent electronic business consultant and author of the book Net
Traveller. Tom is one of the architects of the Commonwealth Government's
Internet and web strategy. The first Web Master for the Australian Department
of Defence, in 1999 he was elected a Fellow of the Australian Computer Society
for his contribution to the development of public Internet policy. Tom is a
director and past President of the Australian Computer Society and a voting
member of the Association for Computing Machinery.
Postscript 7 June 2001
-
Cocoon is a 100% pure Java publishing framework that relies on new W3C technologies (such as DOM, XML, and XSL) to provide web content. The Cocoon project aims to change the way web information is created, rendered and served. The new Cocoon paradigm is based on the fact that document content, style and logic are often created by different individuals or working groups. Cocoon aims for a complete separation of the three layers, allowing the three layers to be independently designed, created and managed, reducing management overhead, increasing work reuse and reducing time to market. The Apache Software Foundation, 1999-2001
-
OpenOffice.org is an Open Source community project building the next generation of office-productivity software. Sponsored by Sun Microsystems, Inc., and hosted by CollabNet, Inc., OpenOffice.org provides the full infrastructure for global, Open Source community work and growth. OpenOffice.org, 2001
- The IEEE is
developing a Recommended
Practice for the Internet - Web Site Engineering, Web Site Management and
Web Site Life Cycle:
Define recommended practices for World Wide Web page engineering for Intranet and Extranet environments, based on World Wide Web Consortium (W3C) and related industry guidelines ... This is intended to provide guidance to web page developers in Intranet (organizational internal), and Extranet (amongst a limited domain of organizational participants) web environments on recommended practices for web page engineering. The objective is to improve the productivity of Intra/Extranet web operations in terms of locating relevant information,and efficient development and maintenance practices.
See also:
This document is Version 2.2, 7 July 2001: http://www.tomw.net.au/2001/eal/notb2b.html
Copyright © Tom Worthington 2001